Having just flown from Sydney AU to Christchurch NZ, my Galaxy Nexus suddenly decided to finally offer me the Android 4.2.2 upgrade.
Since I got the phone in 2012, it’s been running Android 4.1 – I had expected to receive Android 4.2 in November 2012 when it was released by Google since the Galaxy Nexus is one of Google’s special developers phones which are loved and blessed with official updates and source code.
However the phone has steadily refused to update and whilst I was tempted to build it from source again, seeing as 4.2 lacks any particular features I wanted (see release changes), there was little incentive to do so. However after 4.2.2 was magically revealed to me following changing countries, I decided was nagged to death to update and ended up doing so… sadly I wish I hadn’t….
Google have messed with the camera application yet again completely changing the UI – the menu now appears where ever you touch the screen, which does make it easier to select options quickly in some respects, but they’ve removed the feature I use the most – the ability to jump to the gallery and view the picture you just took, so it’s not really an improvement.
Secondly the Android clock and alarm clock interface has been changed yet again – in some respects it’s an improvement as they’ve added some new features like stop watch, but at the same time it really does feel like they change the UI every release (and not always in good ways) and it would be nice to get some consistency, especially between minor OS revisions.
However these issues pale in comparison to the crimes that Google has committed to the lock screen…. Lock screens are fundamentally simple, after all, they only have one job – to lock my phone (somewhat) securely and prevent any random from using my device. As such, they tend to be pretty consistent and don’t change much between releases.
Sadly Google has decided that the best requirement for their engineering time is to add more features to the lock screen, turning it into some horrible borg screen with widgets, fancy clocks, camera and all sorts of other crap.
Crime 1 – Widgets
The lock screen now features widgets, which allow one to stick programs outside of the lockscreen for easy access (defeating much of the point of having a lock screen to begin with) and offering very limited real benefit.
Generally widgets serve very limited value, I use about 3 widgets in total – options for tuning on/off hardware features, NZ weather and AU weather. Anything else is generally better done within an actual application.
Widgets really do seem to be the feature that every cool desktop “must have” and at the same time, have to be one of the least useful features that any system can have.
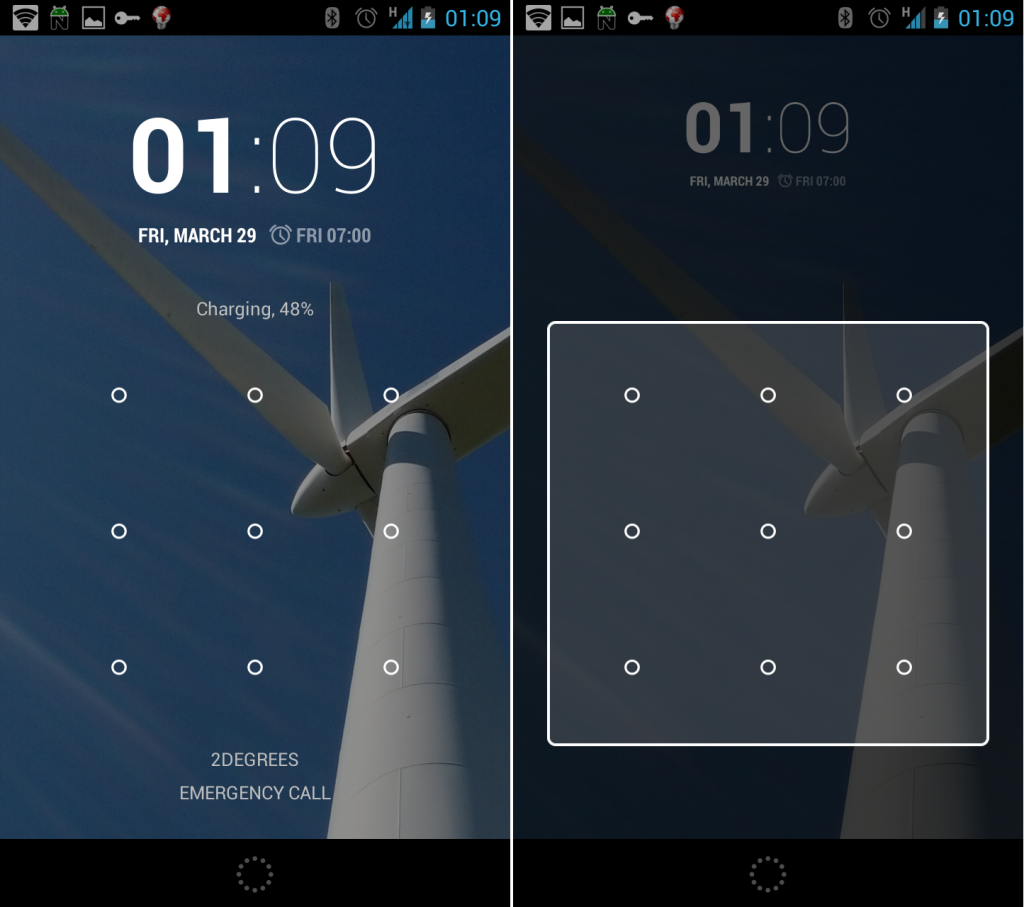
Crime 2 – Horribly deforming the pattern unlock screen
With the addition of the widgets, the UI has been shuffled around and resized. Previously I could unlock by starting my swipe pattern from the edge of the device’s physical screen and drawing my pattern – very easy to do and quick to pick up with muscle memory.
However doing this same unlock action following the Android 4.2 upgrade, will lead to me accidentally selecting the edge of the unlock “widget” and instead of unlocking, I end up selecting a popup widget box (as per my screenshot) and then have to mess around and watch what I’m doing.
This has to the single most annoying feature I’ve seen in a long time purely because it impacts me every single time I pickup the phone and as a creature of habit, it’s highly frustrating.
And to top this off, Android now vibrates and makes a tone for each unlock point selected. I have yet to figure out what turns this highly irritating option off, I suspect it’s tied into the keyboard vibration/tone settings which I do want…
Crime 3 – Bold Clocks
We’ve had digital clocks for over 57 years, during which time I don’t believe anyone has ever woken up and said “wow, I sure wish the hours were bolder than the minutes”.
Yet somehow this was a good idea and my nicely balanced 4-digit 24-hour clock is unbalanced with the jarring harsh realisation that the clock is going to keep looking like a <b> tag experience gone wrong.
I’m not a graphical designer, but this change is really messing with my OCD and driving me nuts… I’d be interested to see what graphic designers and UX designers think of it.
So in general, I’m annoyed. Fucked off actually. It’s annoying enough that if I was working at Google, I’d be banging on the project manager’s door asking for an explanation of this release.
Generally I like Android – it’s more open than the competing iOS and Windows Mobile platforms (although it has it’s faults) and the fact it’s Linux based is pretty awesome… but with release I really have to ask… what the fuck is Google doing currently?
Google has some of the smartest minds on the planet working for them, and the best they can come up with for a new OS release is fucking lock screen widgets? How about something useful like:
- Getting Google Wallet to work in more locations around the world. What’s the point of this fancy NFC-enabled hardware if I can’t do anything with it?
- Improve phone security with better storage encryption and better unlock methods (NFC rings anyone?).
- Improve backups and phone replacement/migration processes – backups should be easy to do and include all data and applications, something like a Timemachine style system.
- Free messaging between Android devices using an iMessage style transparent system?
- Fixing the MTP clusterfuck – how about getting some good OS drivers released?
- Fix the bloody Android release process! I’m using an official Google branded phone and it takes 5 months to get the new OS release??
The changes made in the 4.2 series are shockingly bad, I’m at the stage where I’m tempted to hack the code and revert the lockscreen back to the 4.1 version just to get my workflow back… really it comes down to whether or not the pain this system causes me ends up outweighing the costs/hassle of patching and maintaining a branch of the source.